Table of contents
Prerequisites
An installed TeamSpeak client, if you don’t have TeamSpeak download it from https://teamspeak.com/en/downloads/
While TeamSpeak 5 does indeed have a dark theme built in by default, those of us still using TeamSpeak 3 do not have that luxury.
There are actually two different ways to install TeamSpeak themes (which are really just plugins, they are both installed the exact same way), we’ll show you both ways. First we need to download a dark mode theme, there are a number of the dark themes but the one I personally use and recommend is DarkenTS – Dissension.
Other honourable mentions include:
NekoSpeak (https://www.myteamspeak.com/addons/30f4df31-7e2e-4d09-9d28-40b1bcfa4db4)
NekoSpeak is nearly a black TeamSpeak theme, minus the small amount of gold included
Darcula (https://www.myteamspeak.com/addons/30f4df31-7e2e-4d09-9d28-40b1bcfa4db4)
Darcula is a theme based on the Dark theme for JetBrains products, so programmers amongst you should be very comfortable with this TeamSpeak theme.
These alternatives can both be installed with the exact same instructions.
Option one (nearly) automatic
Press tools => options in your TeamSpeak menu bar and navigate to the Addons panel, when you’re there press “Browse online”.
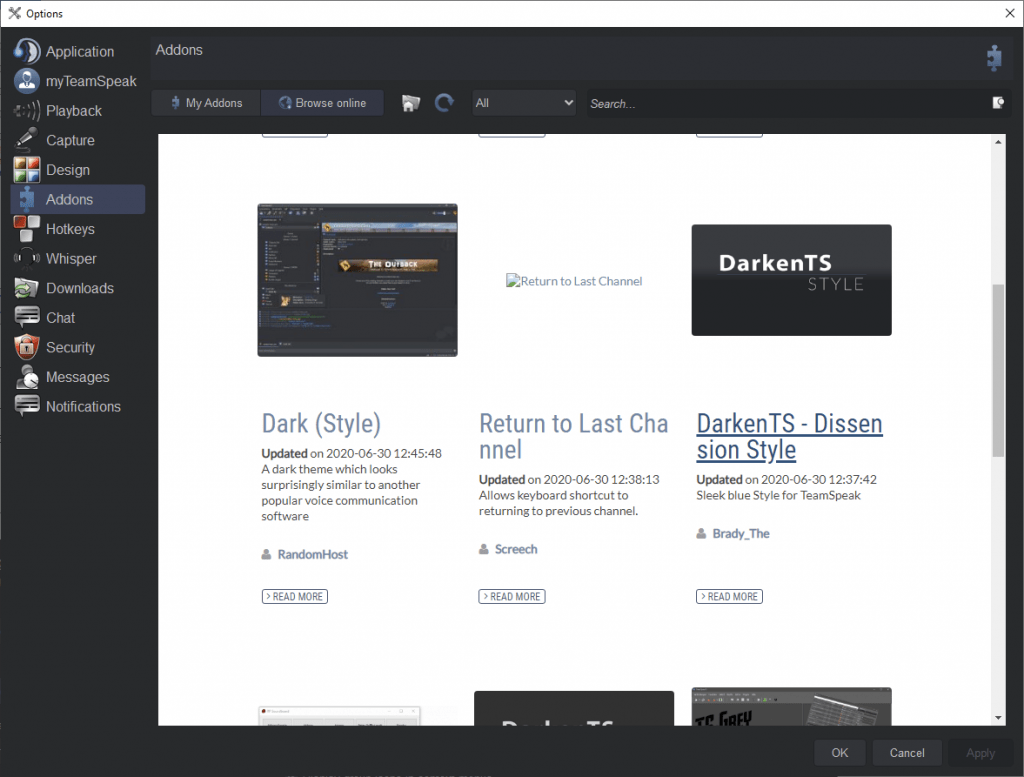
From this screen you can either search for “dark”, at the time of writing it’s near the very top of the default addons you initially are presented with, so you can easily find it by scrolling down a tiny amount.
Click the theme you’re looking to try out
Once the page has loaded click the “install” button
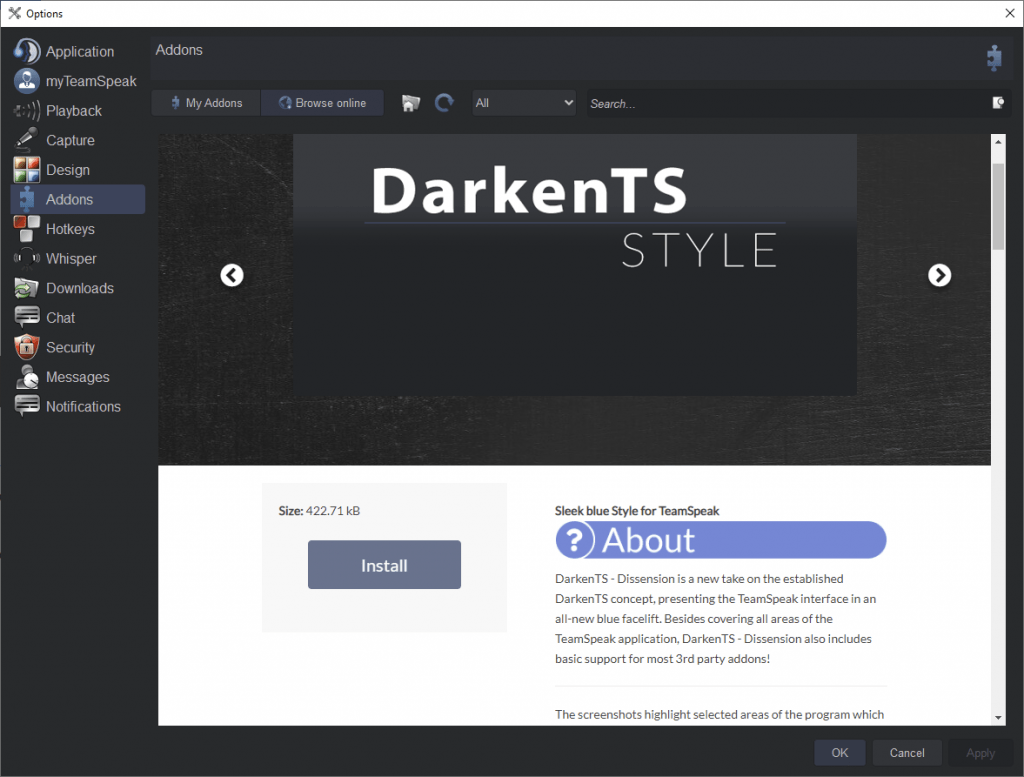
The theme should now be installed and automatically set, if not please see below for the manual way of installing themes.
Option 2 (manual install)
https://www.myteamspeak.com/addons/4a834709-3315-4c53-a80d-b09efd03fce2
Press the “Download” button, and allow your browser to download the file
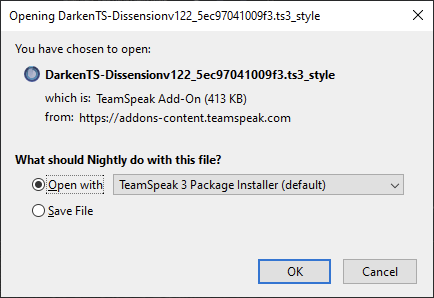
Open the file and you will be presented with a windows that looks something like this :
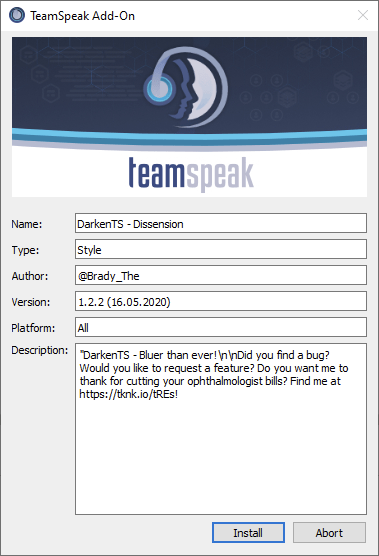
Press Install and restart your TeamSpeak client to complete the install.
After TeamSpeak has opened you press tools => options on the menu bar and navigate to Design, you can then set your preferred theme there, press apply and your client will update with the new theme.
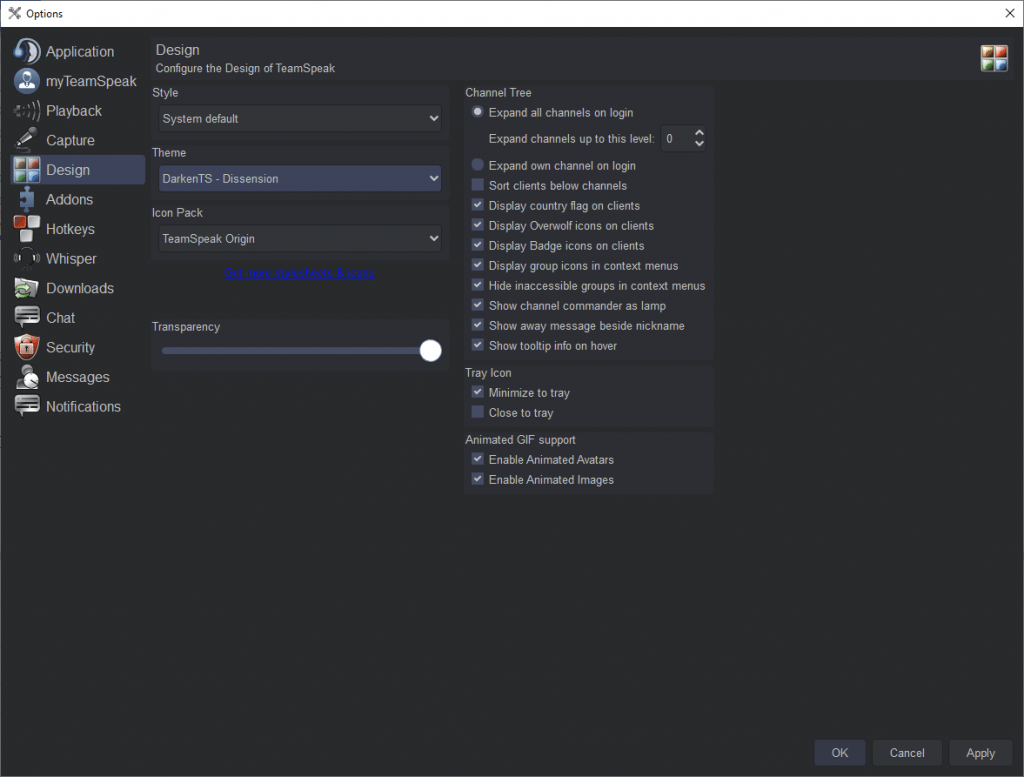
I hope that this explains how easy it is to install TeamSpeaak themes, these same methods can also be used to install TeamSpeak plugins. Need someone to talk to while using your shiny new Dark Mode TeamSpeak? Try finding a server on a TeamSpeak Server List.



Recent Comments